Kiwicon 2038AD Day 2 Summary
Hey all,
I’m back for day 2!
Main talks
Moving Fast and Securing Things - Kelly Ann @kellyxvx
- Talking about Slack secure development lifecycle (SDL) and tooling
- 1300 employees
- 700 engineers
- 400 developers
- 30 security engineers
- 5 product security engineers
- At peak, deploys to prod were happening 100-150 times daily
- Not any more, changed to increase stability.
- Relationship between security and devops…
- Make the engineering team to be security self-sufficient
- Without having to be security experts
- Host weekly security office hours
- Don’t facilitate an adversarial relationship
- Team runs internal “hacktober”, the security awareness month.
- Make security approachable and easy
- Allows the devs to type
/go SDLto begin the SDL cycle- Will be provided a form to request details of the project/feature
- Sends the dev through to a risk assessment form which feeds back to product security
- Allows the devs to type
- “Checklisting for basic items drastically increases the chance that they’ll get done”
- The Checklist Manifesto
- Aviation industry noted performing pre-flight checklist prevented plane crashes.
- Doctors with a checklist have a 50% less likelihood of killing a patient.
- After dev completes checklists, prodsec team performs their review.
- As SDL process has taken effect, bug bounty program has been receiving less severe submissions.
Cyber defence exercises - how to make it cool? - Raimo Peterson
- NATO Co-op Cyber Defence Center of Excellence (CCDCOE) performs
- Research
- Trainings
- Exercises
- Locked Shields
- One week exercise run every year since 2010
- 30 nations, 1000 people attending/contributing
- Live fire exercise
- Real, live red and blue teams.
- Complex, and includes ICS/SCADA.
- Primarily an exercise for the defenders.
- Allows blue teams to test defenses that are difficult to test otherwise
- “Gamified” - Everything is scored, which motivates teams to do better
- Red team balances their attacks arcoss all 24 blue teams.
- Blue teams are VPN’d in from their nation’s capital city.
- Broad, realistic network deployed for each team to defend
- Includes many devices with vulnerabilties
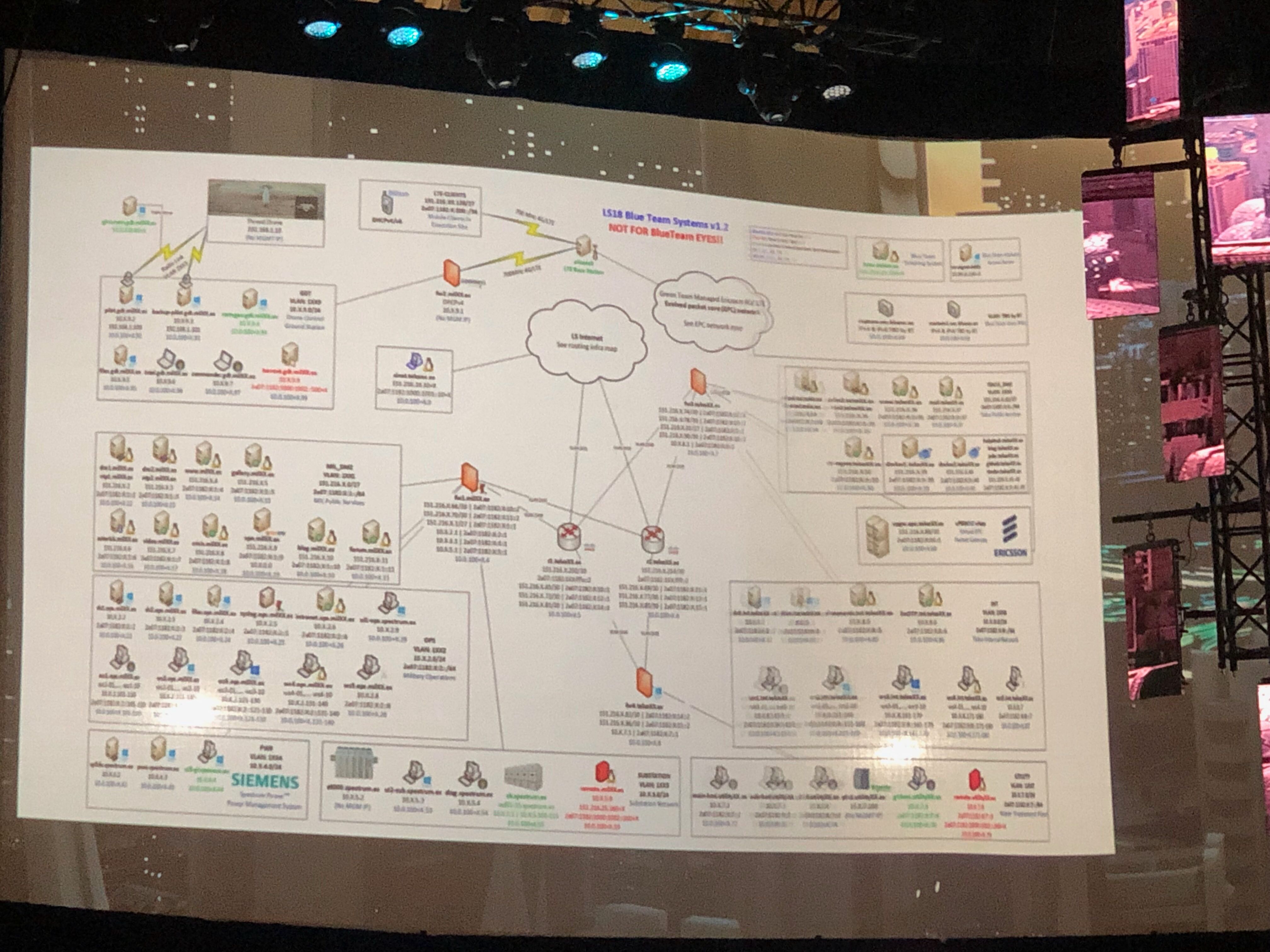
- Includes many devices with vulnerabilties
- Need to cooperate with SMEs from other areas
- e.g. power station/distribution guys
- Build a simplified version of the environment, on servers configured in realistic ways
- Use representative examples that make it easy to see what the impact of an attack is
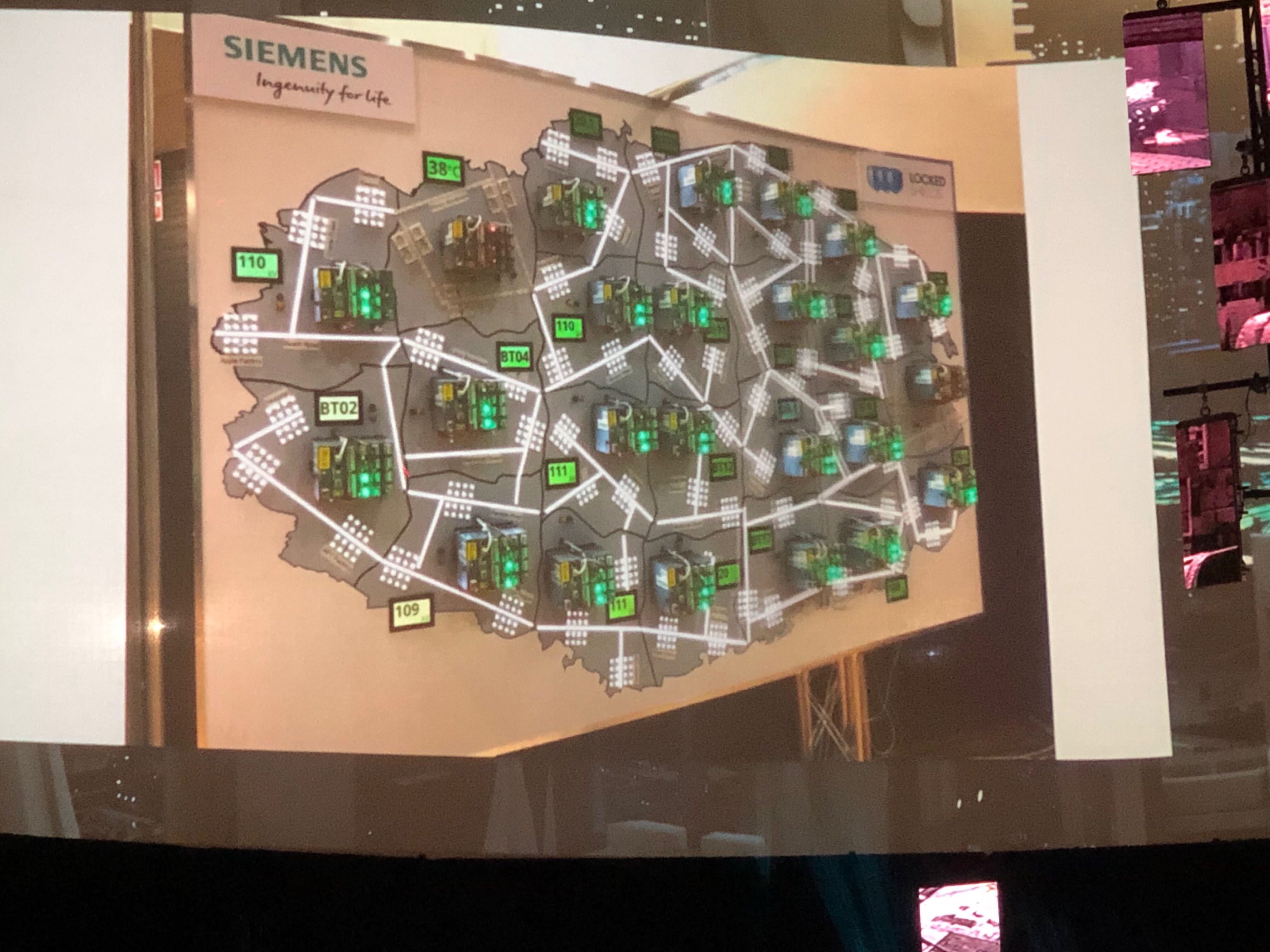
- Provided the teams with a 4G network to play with
- Water purification stations
- Simulated drones
- Industrial systems are more difficult to scale for an environment like this than business systems
- Takeaways
- Simplify but do not oversimplify
- Involve real world experts
- Find win-wins with vendors, otherwise it’s very expensive!
- Systems with nice visualisations may not provide the best learning curve
- Some numbers from LS18
- 4000 VMs
- 2500 attacks
- 1000 people
- 30 nations
- 24 blue teams
- 40 people per blue team on average
Getting Shells from JavaScript: offensive JavaScript techniques for red teamers - Dylan Ayrey and Christian Frichot @xntrik
- Javascript is super powerful
- Actions can still be performed cross-origin, despite the same origin policy (SOP).
- When it’s simple to get SQLi/RCE/LFI (mid-2000s), it’s easy to overlook single-client vulnerabilities (XSS).
- 30% of victims will click a link in their email, only 12% will open an attachment
- Try to focus on the 30%…
- BeEF is a great tool for exploiting this…
- It’s difficult to get browser RCE these days.
- Flash is gone
- Java is gone/somewhat safer
- Browser has access to many important places
- Local networks
- VPNs
- What’s the internal IP of the current machine?
- WebRTC - DOM needs to know local IP, meaning that any JS can get this as well.
- BeEF can do this.
- What other internal hosts are there?
- BeEF can discover this with WebSockets and timing… somehow.
- “Simple” vs “Non-Simple” HTTP request types
- XSS
- If you find XSS you can
- Do anything the user can do on the page
- Steal data
- Change state
- etc….
- XSS is still #1 on HackerOne, by far.
- If you find XSS you can
- Recon of internal hosts
- Rapid7 Project Sonar
- Releases DNS/HTTP/SSL/Port scan info of the Internet periodically
- Can be useful for passive recon
- PassiveTotal
- Can drill in to other WhoIs records that share the same values
- If contactEmail is x@x.com, find other records that have x@x.com
- Internal open source tools can be discovered from DNS names
- Can be valuable, because a host that isn’t directly available becomes white box
- Tend to be less patched/protected than externally accessible services
- Rapid7 Project Sonar
- DNS rebinding allows you to bypass same origin policy
- You can’t target SSL only services though :(
- ServiceWorkers are helpful here as well
- You get to run arbitrary JS for up to 30min after the tab was opened, even after it has closed.
- In Closing
- Browsers have accsss to multile contexts
- Use this as part of assessments
- Recon for internal systems, especially open source software
- Look for vulns in them
- New browser features often provide new tools for attackers (ServiceWorkers/WebRTC/etc.)
- Secure your internal apps!
- Browsers have accsss to multile contexts
Overwatch Cyber-Espionage Tool - Wayne
- Built a Windows implant tool - Overwatch Offensive
- Gathers digital espionage from high value targets
- Inspired by Vault7 Wikileaks documents talking about C2
- Takeaways:
- Don’t be afraid to embark on a large project/goal
- You will definitely learn new things making something yourself, even if people have made the same thing before.
- The satisfaction that you get when you reach your large goal will be immense.
Tracing the Watchers: practical tooling - Paul McMillan
- Got here late, so missed the beginning…
- Researched, and created tooling for locating transmitters on a live public safety radio system
- Any radio transmitter is inadvertantly transmitting it’s location if somebody it listening propeprly.
- Used a bladeRF for all of the RX nodes
- A lot of this stuff kinda went over my head, but it was interesting :P
Lightning Talks (15min)!
Arbitrary code execution, I choose you! - Sarah Young @_sarahyo
- Vulnerabilities in games consoles
- CVE-2018-6242 - Vuln in NVidia Tegra X1 chips, which affects the Nintendo Switch
- Chip enters USB recovery mode
- Chip loads and runs code from recovery mode before checking it’s signature…
- May brick your switch! Try at your own risk!
- Created/discovered by @fail0verflow
- Nintendo will be releasing a new switch next year, which will likely fix this
- NES lockout chip
- Nintendo used to have really strict policies on what games could run on their platform.
- You needed a Nintendo (“Lockout”) chip in the cartridge to be able to have your game run
- “Nintendo Seal of Quality”
- US Patent office handed over the Nintendo patents for the lockout chip when Tengen/Atari asked…
- Lots of sueing ensues.
- Pokemon #000 - Missingno
- Glitch Pokemon that was used as a beta test.
- There were only 151 pokemon, but 256 slots.
- Some of them needed to be filled.
- Why?
- Programmers forgot to assign which pokemons show up on a particular strip of water.
- It instead looked at another bit of memory under certain conditions, which would mean you could encounter different pokemon depending on your trainer name.
- Takeaways
- Need to tell relatable stories
- Malicious parties will go to great lengths to achieve their goals
- Not always going to be technical!
Mūrere me te haumarutanga - Chris Cormack @ranginui and his dad
- How do infosec terms/concepts translate into Maori?
- Murere - Be clever, intruding
- to hack, hacker
- Haumarutanga
- haumaru - safe, risk free
- security
- The act of being risk free
- Wheinga
- adversary, opponent
- Whakahotuhi whakawhiti pae
- To script across site
- XSS
- Whakeke waengarahi
- attack
- intervening space
- Man in the middle
- Whakaeke pureirei engaenga
- Buffer overflow attack
- Whakakore ratonga
- deny service
- Denial of service
- Pkahatanga papori
- Social engineering
- Hitinihanga
- To fish
- Deceive, trick
- Phishing
- Whakamatautau ngoto
- Test, try out
- to penetrate
- Penetration testing
- Rehita turaru
- Risk register
- Hinu nakahi
- “snake oil”
- virus scanner :P
- Whakahaere tapi
- Manage, control
- Patch, repair, mend
- Whakaeke ra orite
- attack
- day
- same
- 0day
Red Cell - Mimicking Threat Actors for Realistic Responses - Brendan Jamieson
- Red cells are insider threats at Google.
- Similar to red teams.
- Except they:
- Mimic real TTPs from specific actors
- Detection & response zero-knowledge
- These help create better stories and better results
- Who do we want to mimick?
- We want to mimick everything, down to custom tools, exfil, and leaving behind artefacts
- With a red team, response teams know of the exercise, but detection teams don’t
- With a red cell, neither detection or response teams have knowledge of the exercise
- Adds pressure, which helps to get accurate responses
- Having people from detection and response become attackers can bring a fresh perspective
- Difficult to emulate an attacker’s time zone if it’s drastically different to yours.
- Simultaneous cells can be taxing on the blue team
- Write a postmortem per team when complete
- Want to learn from the exercises in a blameless manner.
- Blue team postmortem
- Summary, timeline of events
- What went well?
- What went wrong?
- Red cell postmortem
- Summary, and timeline
- Goals
- Attack vectors
- Controls related to mitigation and detection
- What is a realistic threat model for your organisation?
- MITRE ATT&CK framework contains real public TTPs.
Set Theory for Hackers - @pruby
- What is a set? A group of things.
- Wasn’t able to keep up with notetaking for this one :P
- If one user reports an email, and it is blocked immediately.
- Generally, an exists statement will win against an all statement.
- True for all vs. true for any.
- Models can help.
Hacking and the law: The year is actually still 1998 - Felix Geiringer
- Legal system is 40 years behind with regards to hacking.
- When “Hackers” was first released, there were 0 computer crime laws on the books at all in NZ.
- The rest of the world was very similar.
- Commission report showed up in 1999.
- The current laws are very broad with regards to “accessing a computer system”.
- These laws currently fit in the “property” section of the law.
- 249 - Accessing computer system for dishonest purpose
- Almost all computer crimes have come under this section.
- Extremely broad.
- You don’t need to know whether you don’t have permission.
- 250 - Damaging computer system
- “Modify any data” can be caught under this section.
- Half of computer crimes charged are actually just fraud.
- Things that are actually computer crimes don’t fall under the computer crimes law.
- Using a computer to commit a civil copyright violation becomes a crime, according to Kim DotCom’s latest case.
- Breaching terms and conditions could end in the same way…
- Broad laws allow judges to interpret them in whatever way they want in order to get the outcome that they want…
Digital identity: decentralised and self-sovereign - Martin Krafft @martinkrafft
- What is identity?
- Context-specific collection of attributes about you
- In continuous flux
- Accounts are models of your identity.
- These models grow inaccurate as things change.
- SSI
- Identities are identified by a DID
- Trustless peer-to-peer relationship between DIDs
- Use VC (verifiable credentials) to establish trust
- e.g. What is your name, what is your address.
- Correspondent defines the needs they have of you to trust you
- You accumulate the trusts in your “wallet”, and authenticate to the correspondent.
- Blockchain is not a trust root
- BaaS - Blockchain as a solution.
- Building trust is hard
- How do you find who you want to trust, and verify that they are who they say they are?
- Needs for bootstrapping trust
- Trasparent
- Parametrisable
- Easy and intuitive
- Democratize
- Trust is the currency of the future (not Bitcoin)
Martin works at keyp.io
The day the carnival came to town - David Hood
- Lauren Southern + Steven Molineaux were planning to come to NZ.
- David analysed twitter messages regarding this controversy.
- Lots and lots of foreign (non-NZ) people were interested in this situation.
- Build a cluster of indicators that a fascist likes an account.
- Maori are discriminated against, but they also have traction with some in power.
Testastretta Operetta - Denis Andzakovic - DoI - @0x446f49
- Ducati history
- Original Ducati were cheap, reliable commuters for post-war Italy.
- Won some races, people wanted to buy them.
- Talk on hacking Ducatis.
- Ducati security
- Steal motorcycle
- Impact motorcycle to damage the user
- Lock & Key
- Lock & Key - Immobilizer - Mutual auth between ECU and Dashboard
- Replace the ECU, and bike will go into lockdown mode and won’t start.
- Immobiliser can be bypassed
- Connect to CANBUS network
- Yell IMMOBILISER IS OFF really loud
- Bike will start
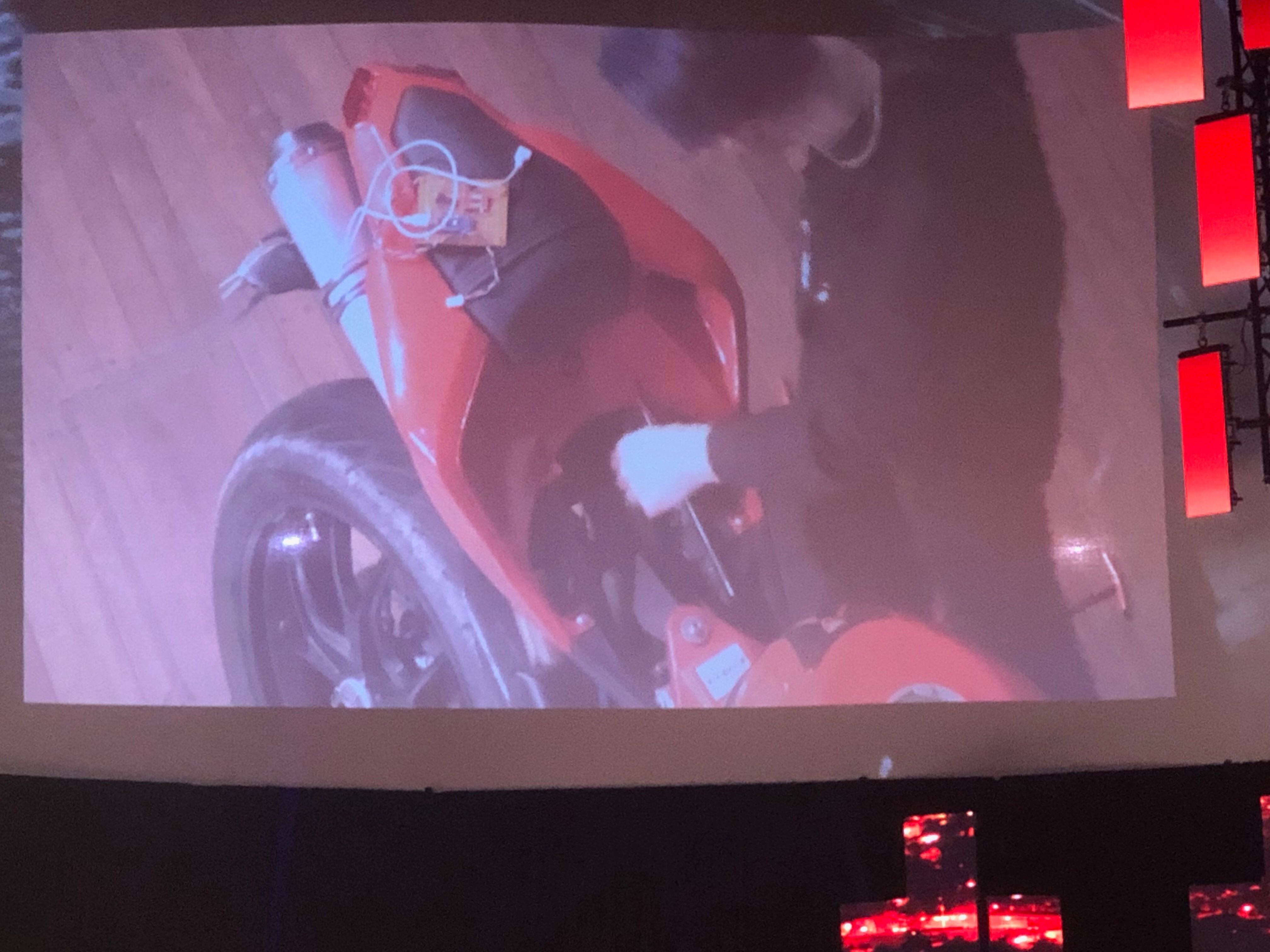
- Firmware extraction
- Volkswagen KKL adapter works for outputting onto the Ducati K-Line wire.
- Need to authenticate using a challenge response protocol to get into diagnostic mode.
- Technology is getting more sophisticated
- Information regarding this technology is getting fewer and fewer.
- This makes it much more difficult for people to look after their own bikes.
- Full research
Server Room Selfies - Logan - @InfoSnekNZ
- All security is hard
- PhysSec is apparently even harder…
- Target #1
- Full red team
- Everything is in scope
- Only 1 week to go
- Critical national infrastructure
- Physical compromise can lead to DA, even if network is reasonably locked down
- Bash bunny slurping hashes from Windows machines.
- Target #2
- Physical assessment only
- Highly sensitive data
- Many open doors, or poor controls
- Designers considered the user experience, but weren’t qualified to think about the security implications.
- Target #3
- Gone through a rapid period of growth, meaning they lacked some structure
- Fairly open scope
- Wear your dodgy visitor sticker upside down.
- Sometimes, in order to get an access card, you just need to ask…
- Needed to review their visitor kiosk - there was no network segregation/etc.
- Needed to improve staff security awareness - visitors being escorted at all times.
- Even if you’re a red team, you need to look at your own orgs physical security..
- Quite a funny physsec storytime talk.
Final numbers
Here are what Kiwicon cost…
- Total Cost: $400K
- Ticket Sales: $220K
- PWYW: $5918
- Highest PWYW: $500
-
Sponsorship: $10K
- Venue Cost: $50K
- AV/Pyro: $150K
- Merch: $47K
Beer was marked up by venue by 200%, up from 100% last year, crazy!
This was my first Kiwicon, and I thought it was great!
I’ll definitely be back next year for Kiwicon 2039, if the Crue will be.
Thank you very much to everybody that helped put it on, including the speakers, volunteers, crue, and sponsors!
XORcat

